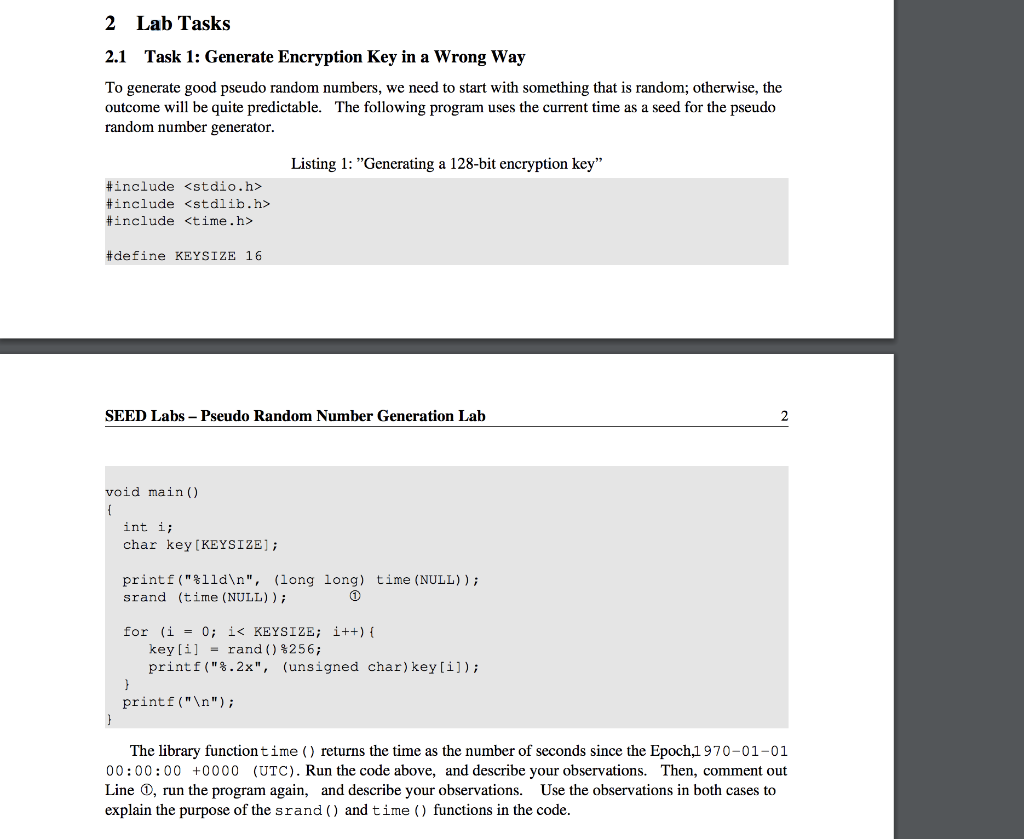
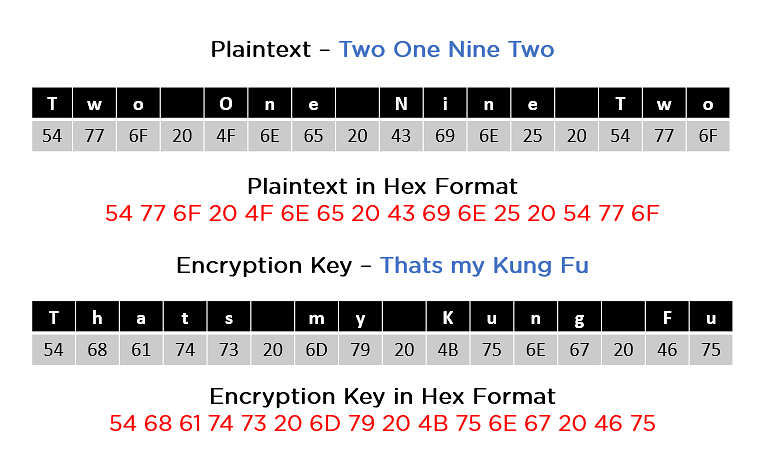
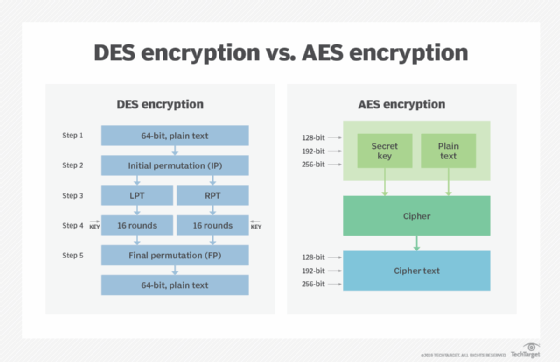
An Analysis the Big Data Security Based on Hadoop Framework Using Hybrid Encryption Technique - Ignited Minds Journals

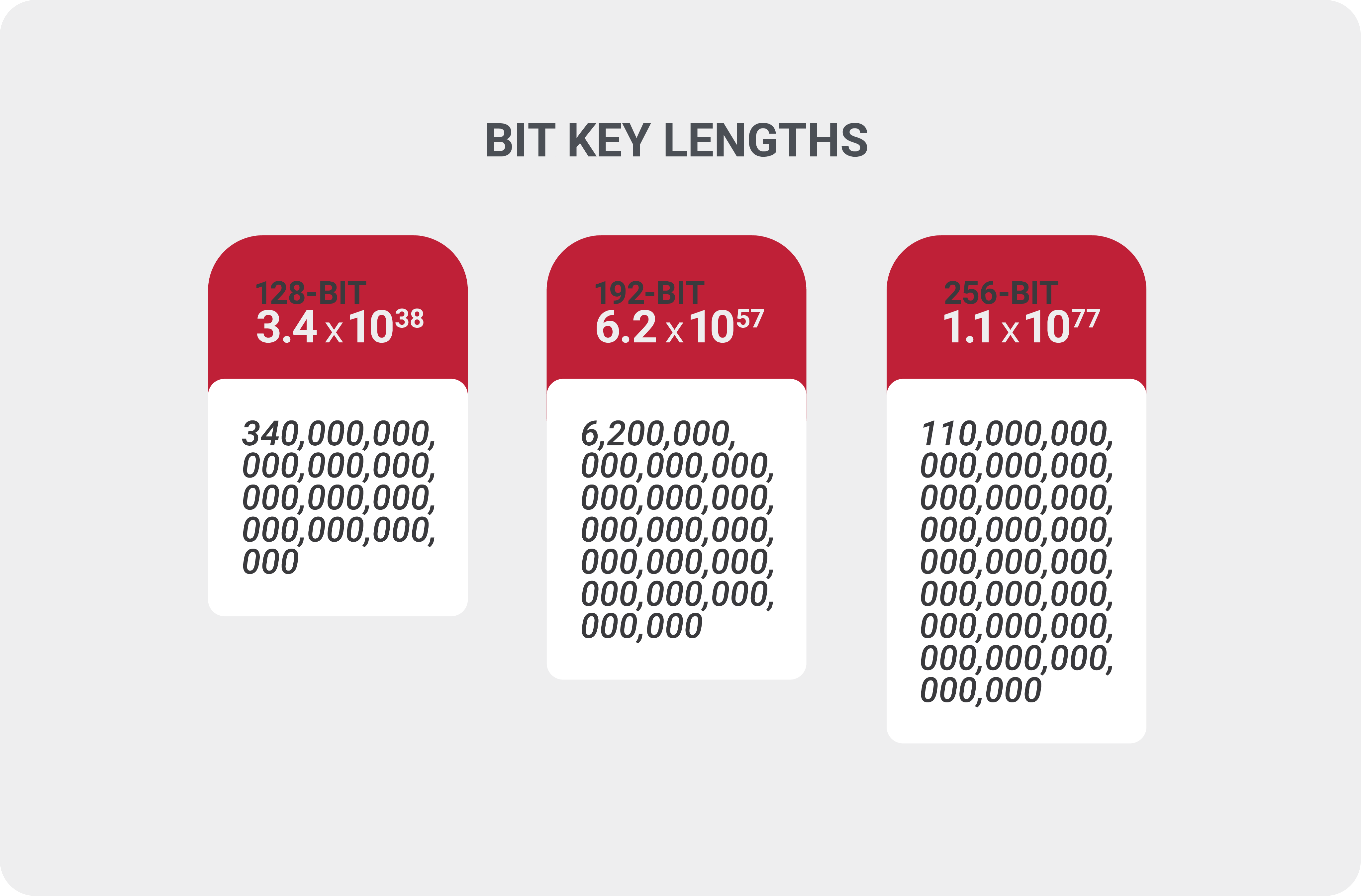
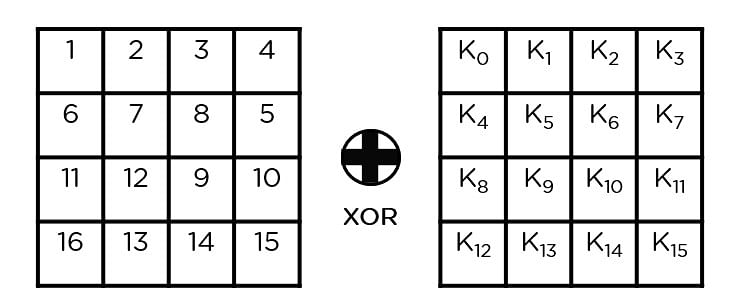
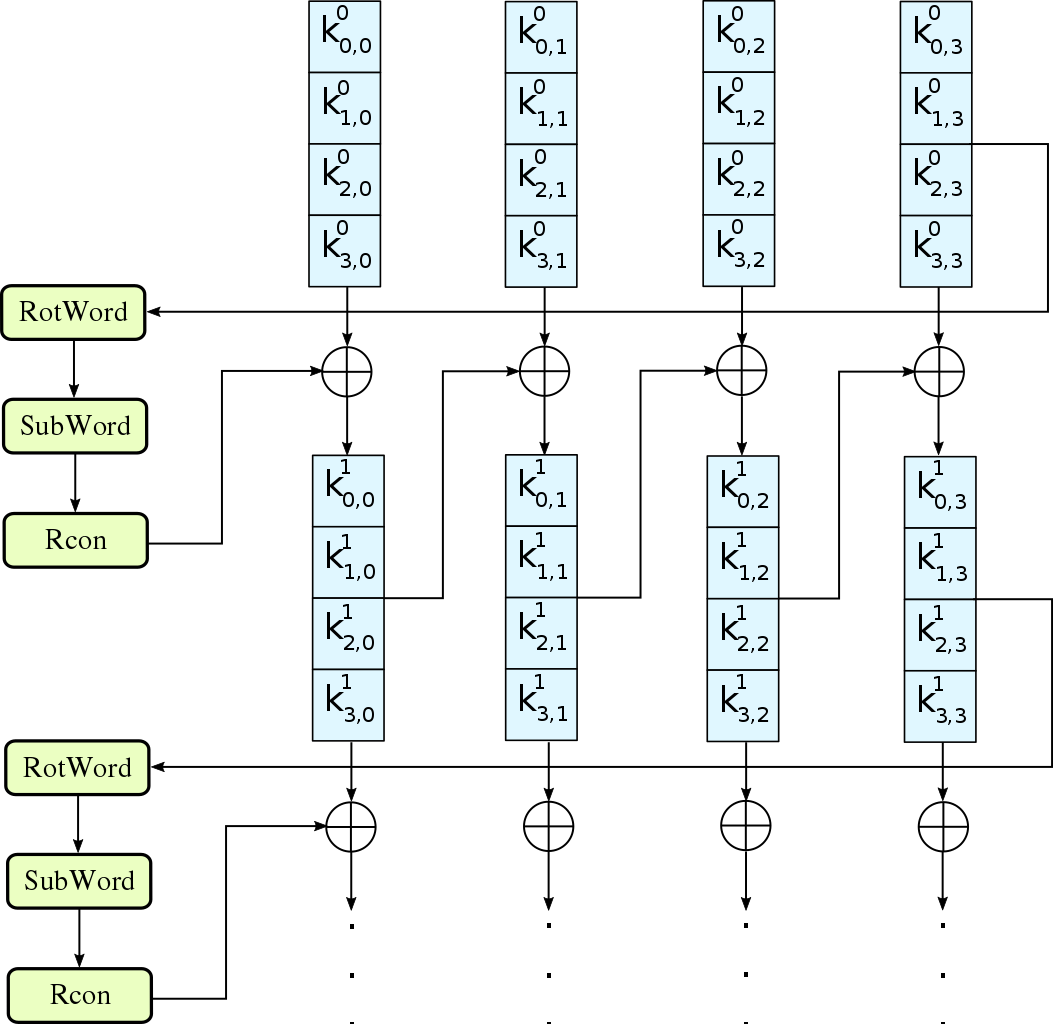
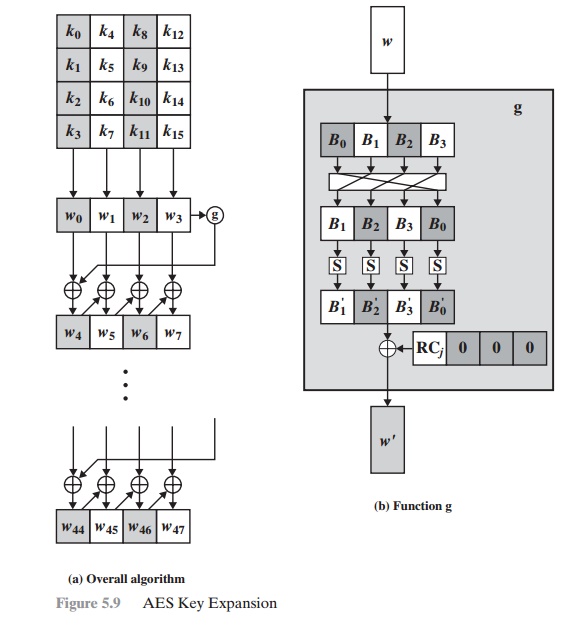
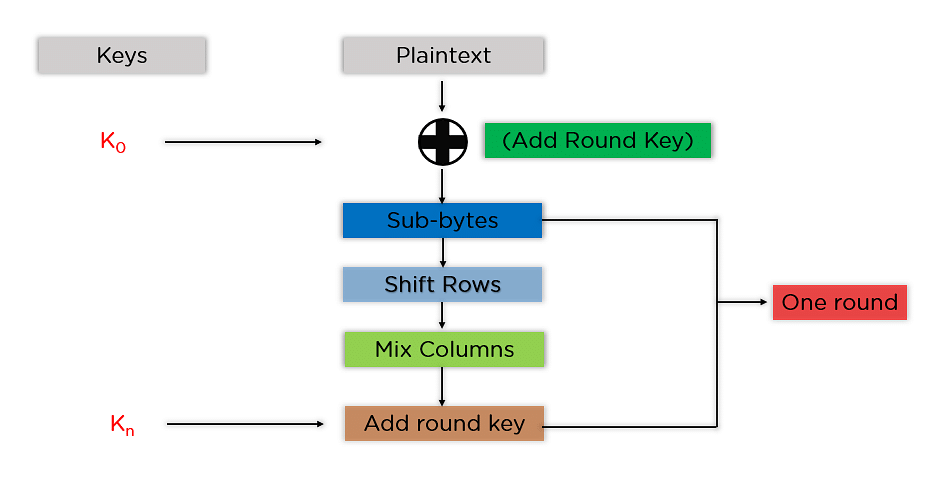
Figure: Structure of AES III. Implementation The AES algorithm is based... | Download Scientific Diagram

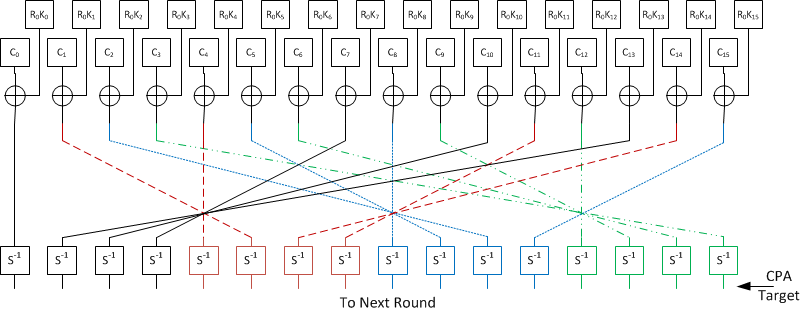
the diagram of A5/3 generator a. "Kasumi is a block cipher produces a... | Download Scientific Diagram