Cryptopals: Exploiting CBC Padding Oracles | NCC Group Research Blog | Making the world safer and more secure
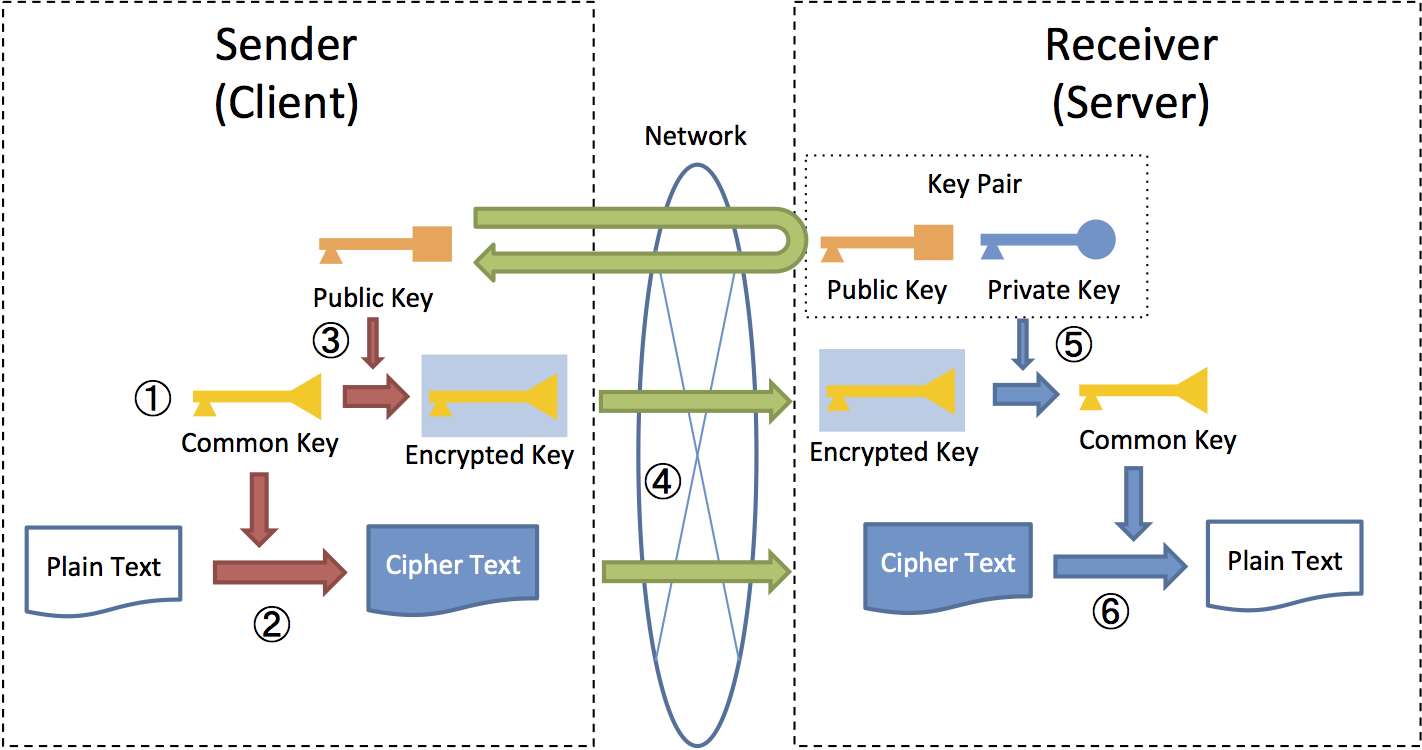
9.8. Encryption — TERASOLUNA Server Framework for Java (5.x) Development Guideline 5.3.1.RELEASE documentation
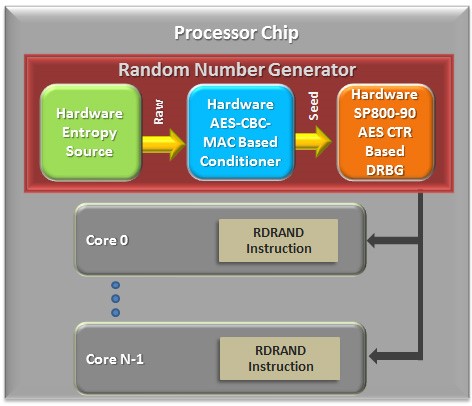
Intel® Hardware-based Security Technologies Bring Differentiation to Biometrics Recognition Applications Part 2 - CodeProject
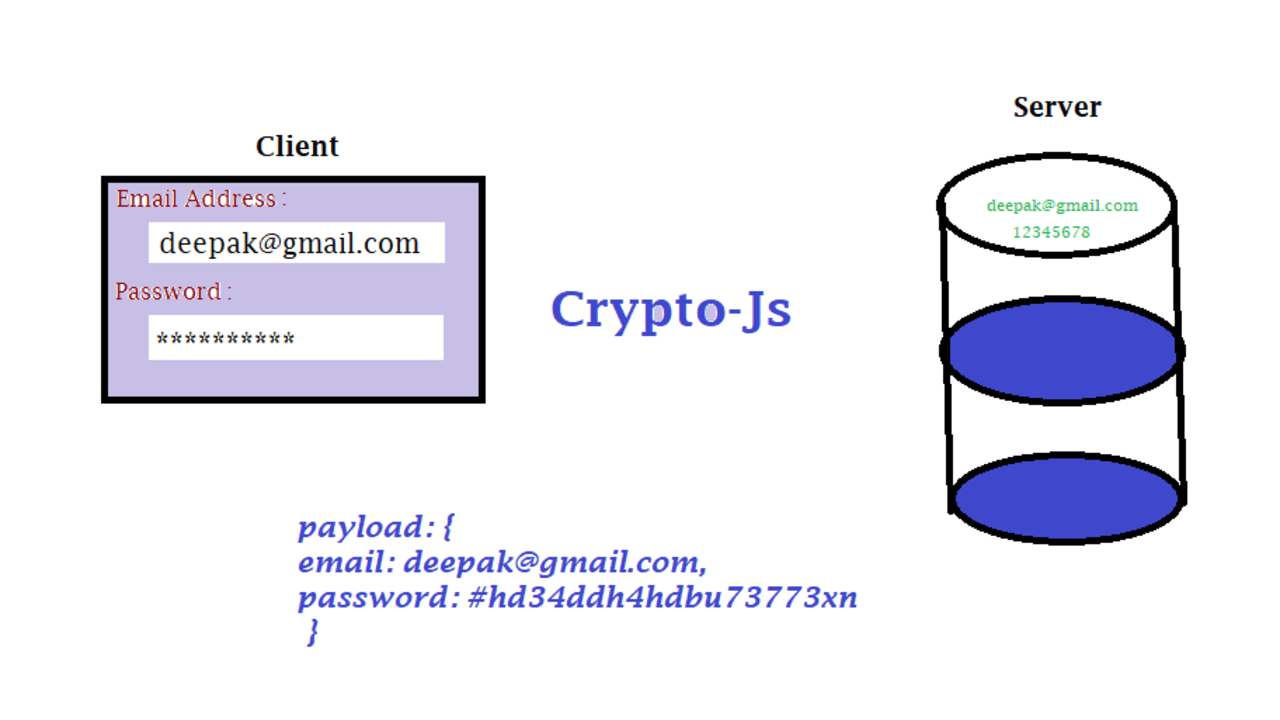
End-to-End Data Security:Shielding API Payloads through CryptoJS and Java AES-256 Encryption” | by Shivam Jaswal | Medium