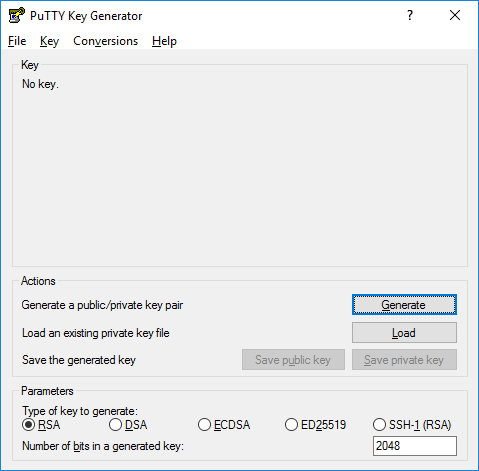
How to install and use puttygen to create new key pairs and change passphrases. Installing keys on server, managing SSH keys.
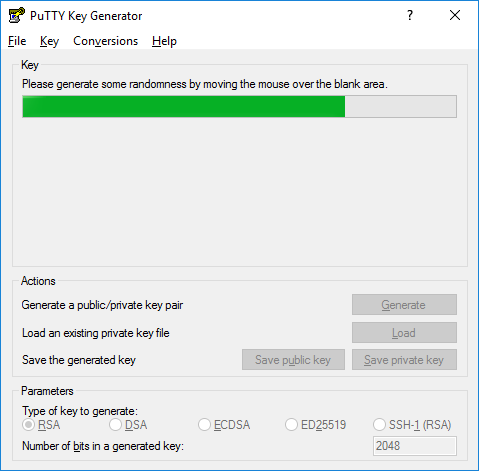
How to install and use puttygen to create new key pairs and change passphrases. Installing keys on server, managing SSH keys.
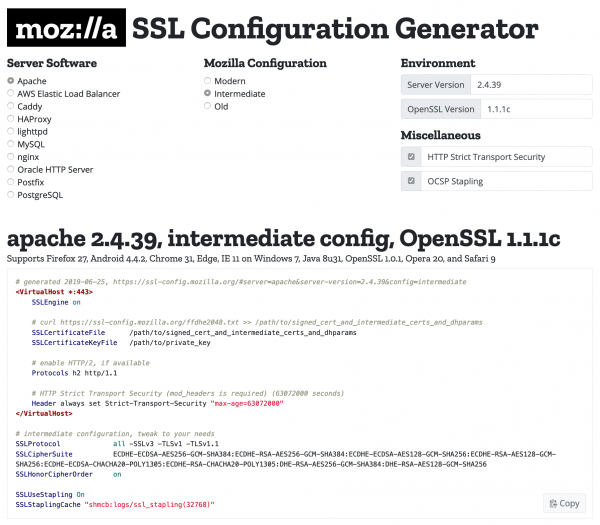
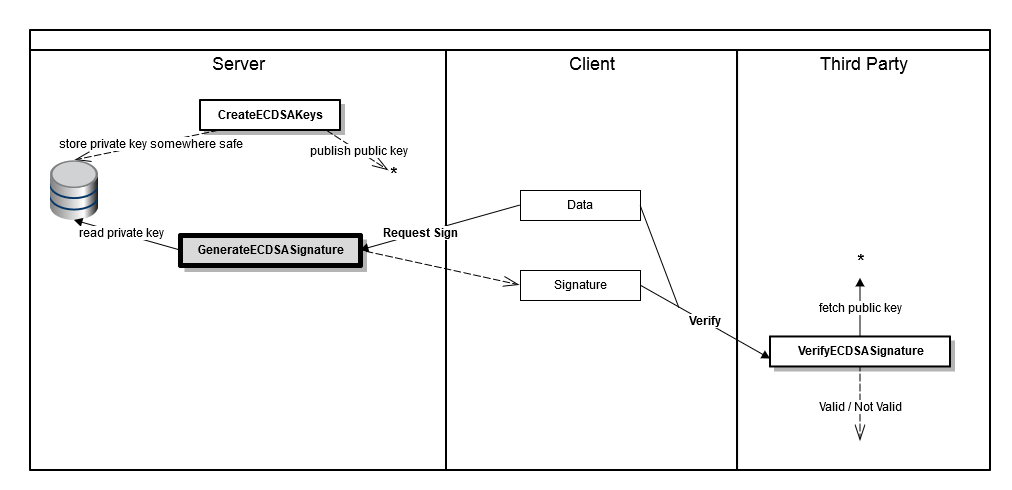
HOW TO: Setup Private Key Authentication using ecdsa-sha2-nistp256 algorithm with the File Processor Connection in CDI

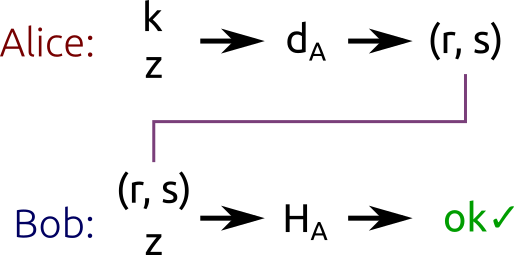
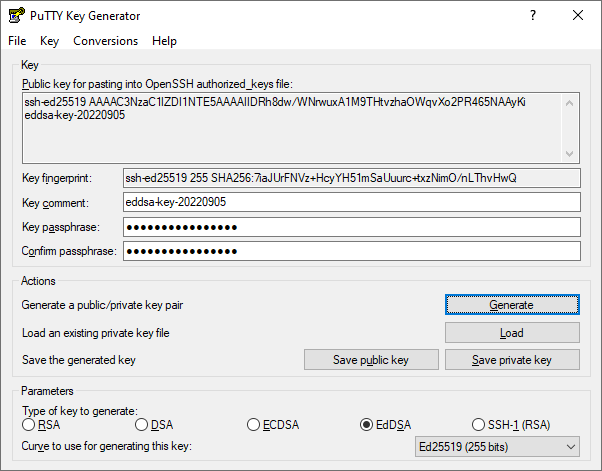


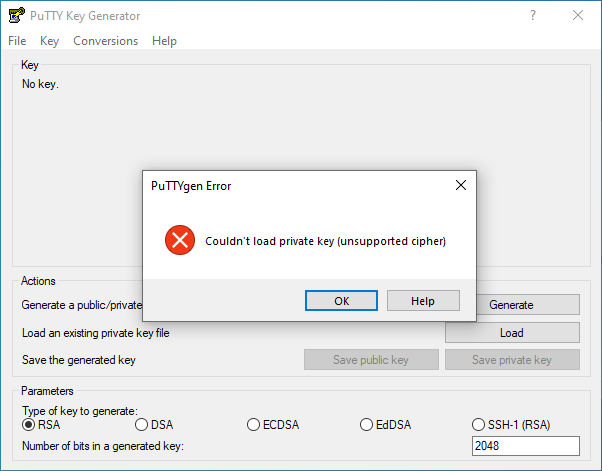

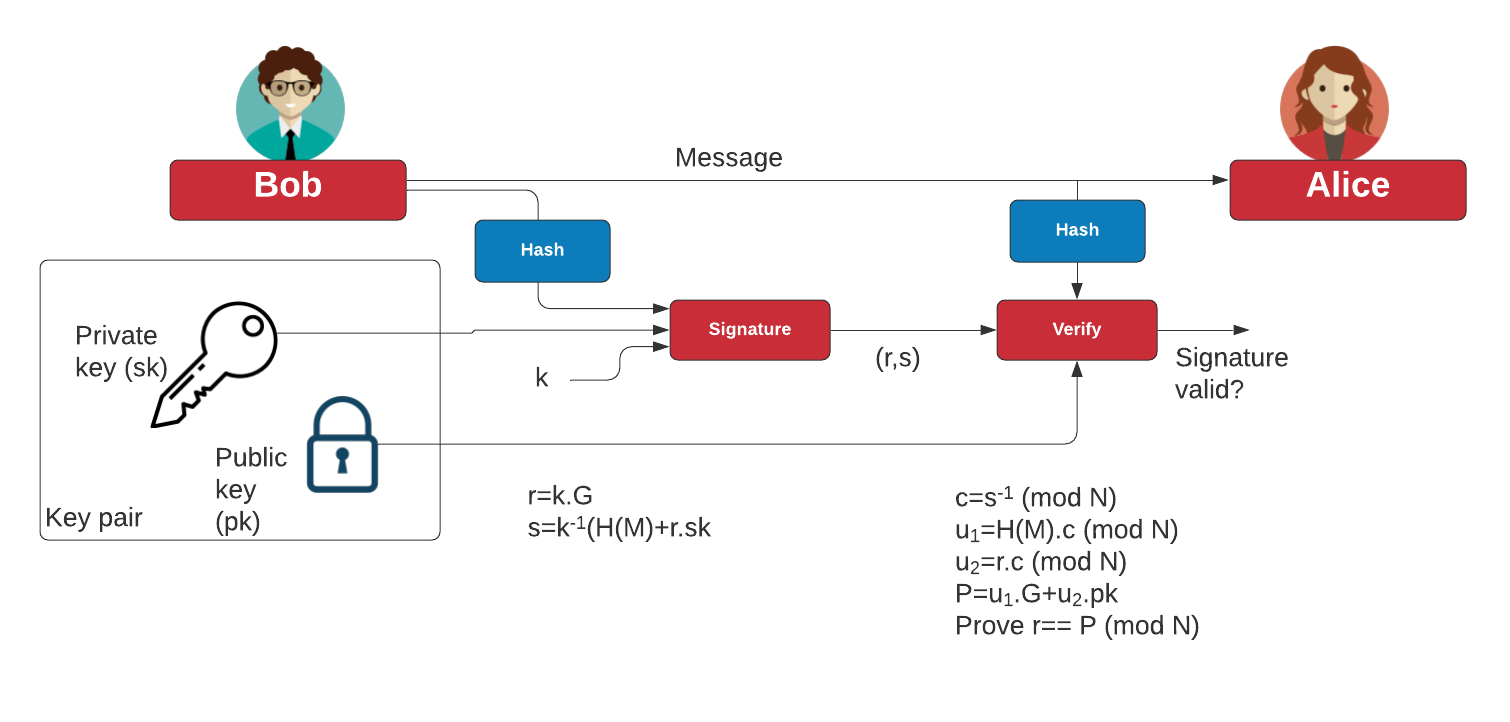
![PDF] Evaluation Report on the ECDSA signature scheme | Semantic Scholar PDF] Evaluation Report on the ECDSA signature scheme | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dcdf334163775459009bc5ed8726c5937615e1ae/8-Figure1-1.png)
![PDF] Evaluation Report on the ECDSA signature scheme | Semantic Scholar PDF] Evaluation Report on the ECDSA signature scheme | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dcdf334163775459009bc5ed8726c5937615e1ae/9-Figure3-1.png)